Last post https://techbyjeff.ghost.io/setting-up-sso-with-entra-and-portainer-oauth-2/ I showed how to set up SSO with Oauth, and it was super straight forward.
With OIDC, or OpenID Connect, we can still set SSO up without sweating too much. I'm going to demonstrate this using Proxmox as it's the hypervisor I migrated to for my homelab VMs after Broadcom's decision to kill ESXi for home use.
We're going to start off in our Entra portal and go to Applications -> App Registrations -> New Registration.
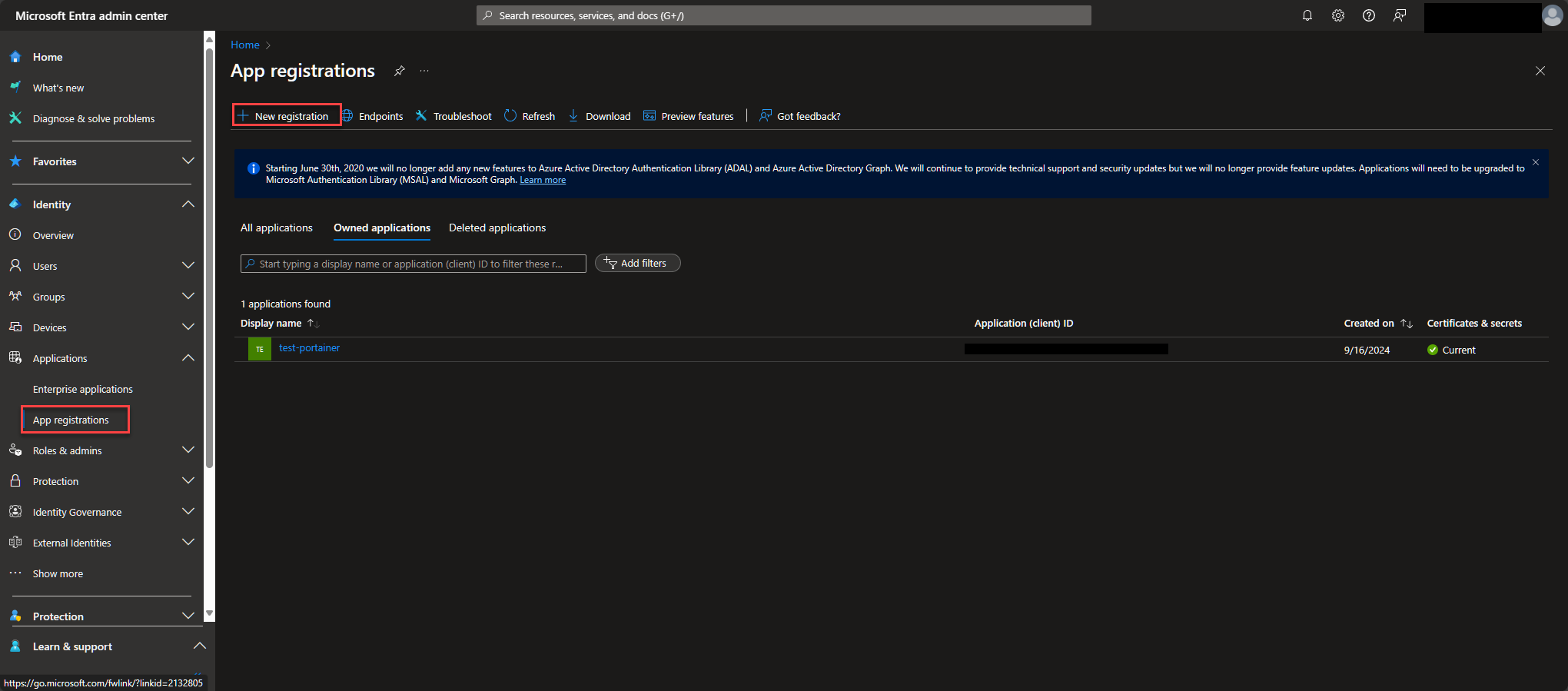
Fill out the name, select the single tenant option, and then web dropdown and fill out the url that hits your PVE login page, including port if necessary and then click next.
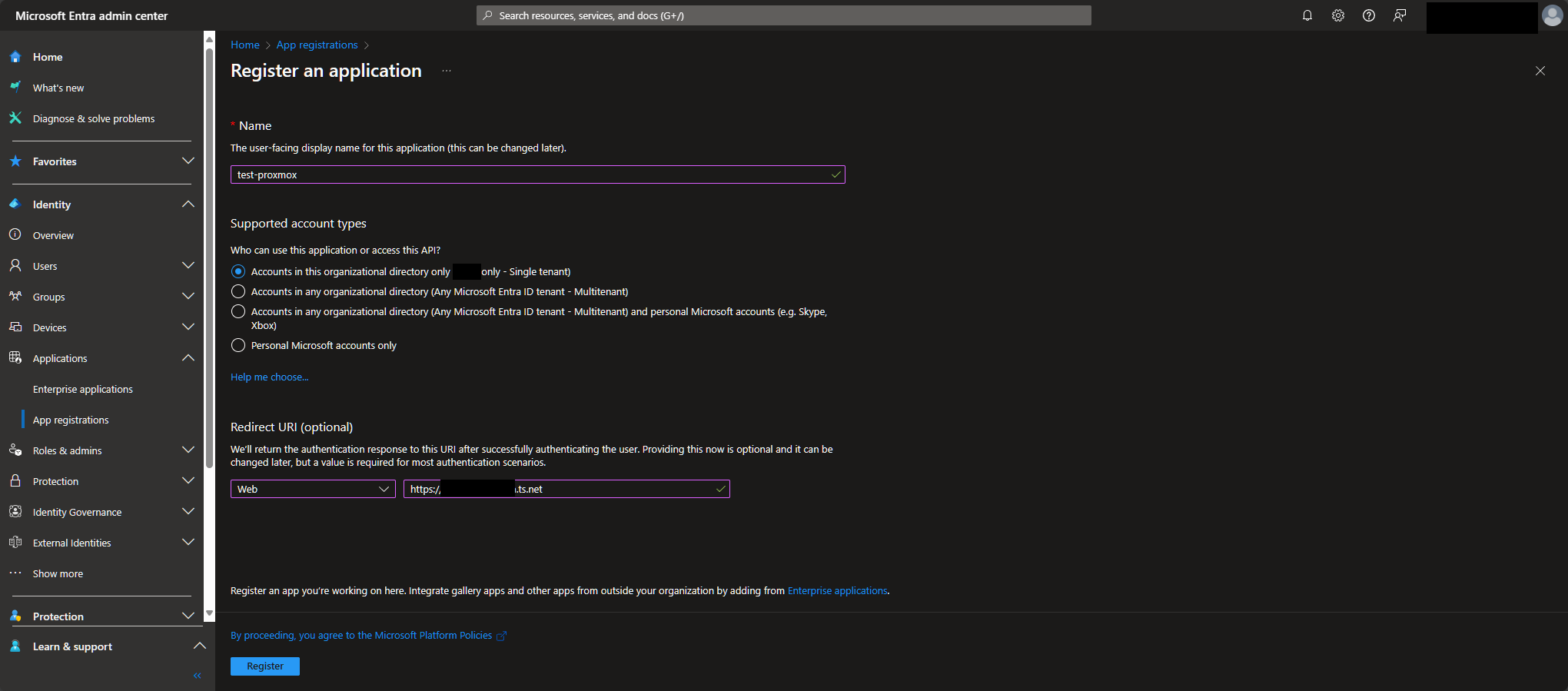
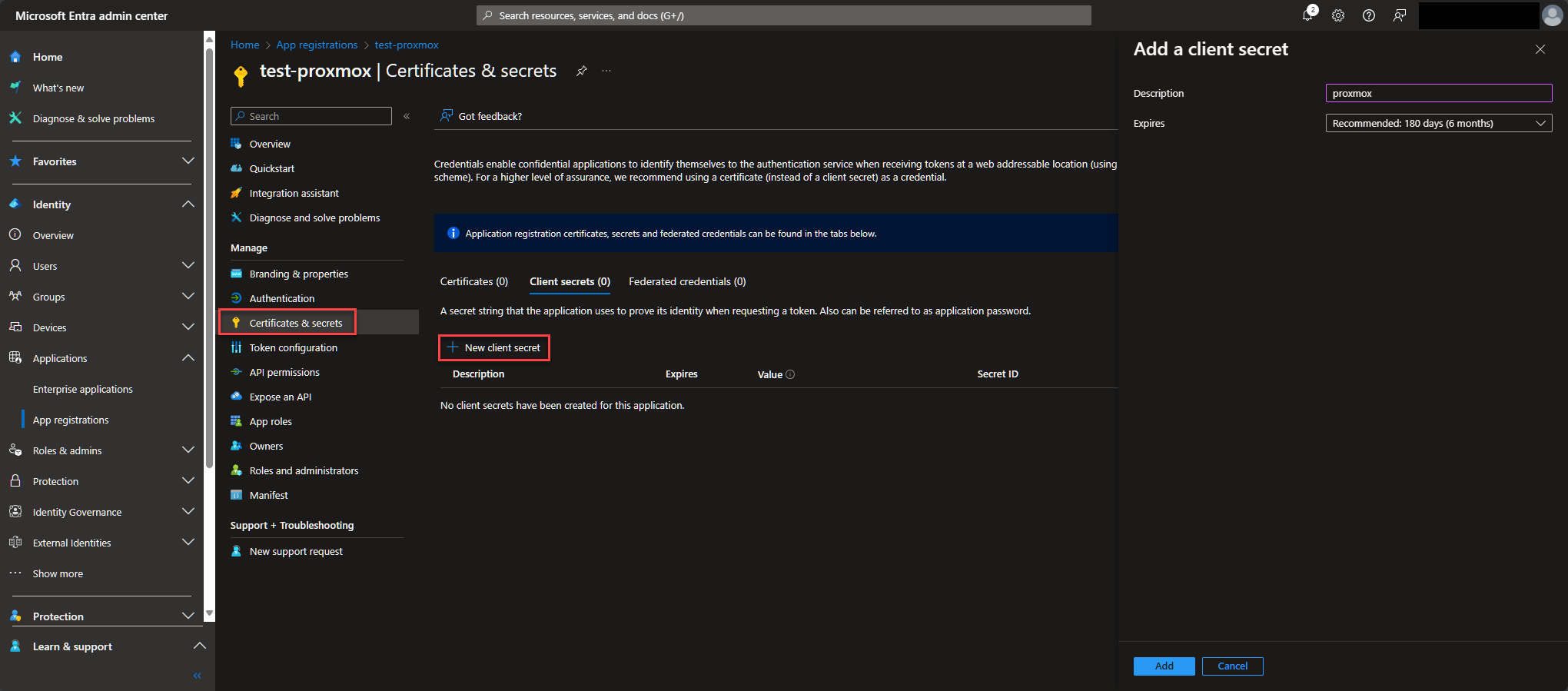
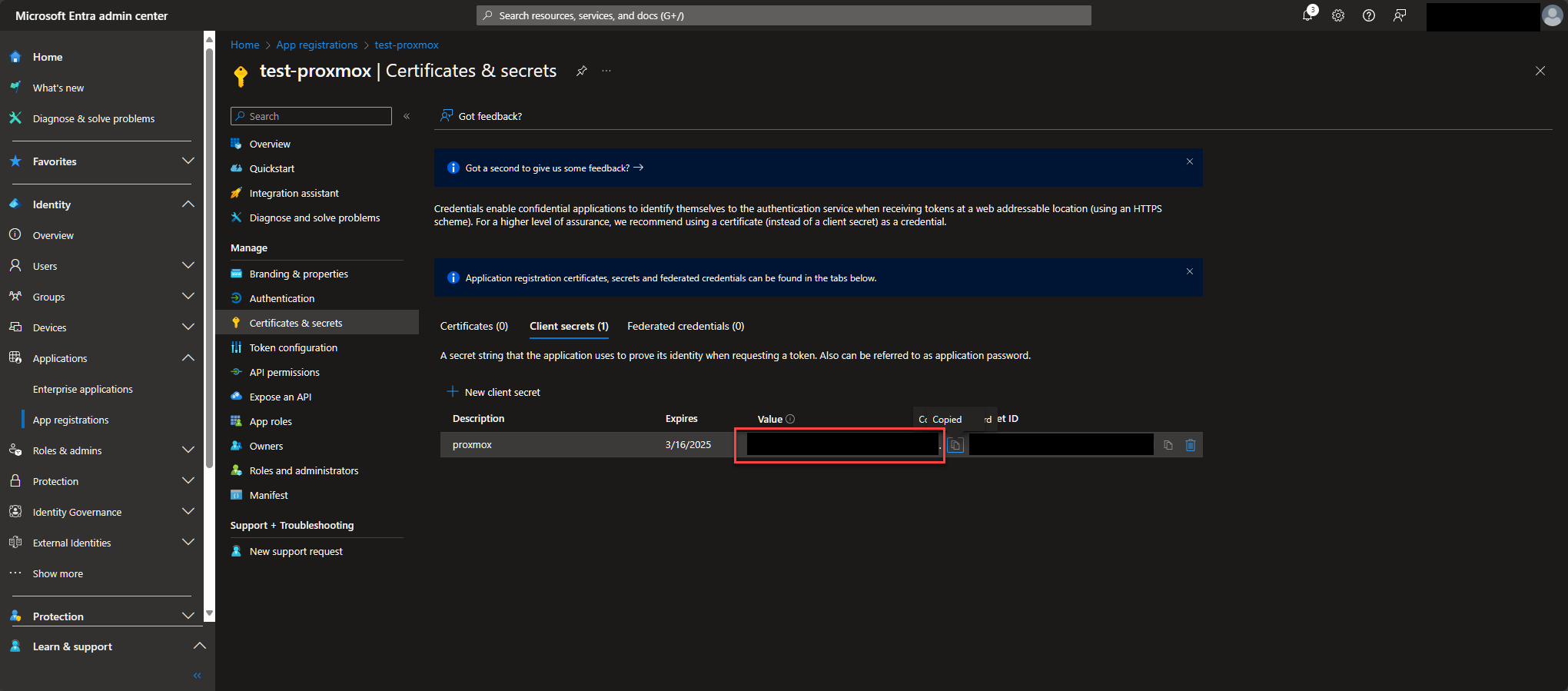
Once it's made, go to Certificates & secrets -> New client Secret. Enter your description and dropdown for how long you want this secret to last. Click on Add when done and record the secret's value as it will only be shown this one time. We haven't gotten there yet, but this is going to be used in Proxmox's Client Key field.
Next go to overview and record the Application (client) ID. This will be used in Proxmox's Client ID field.
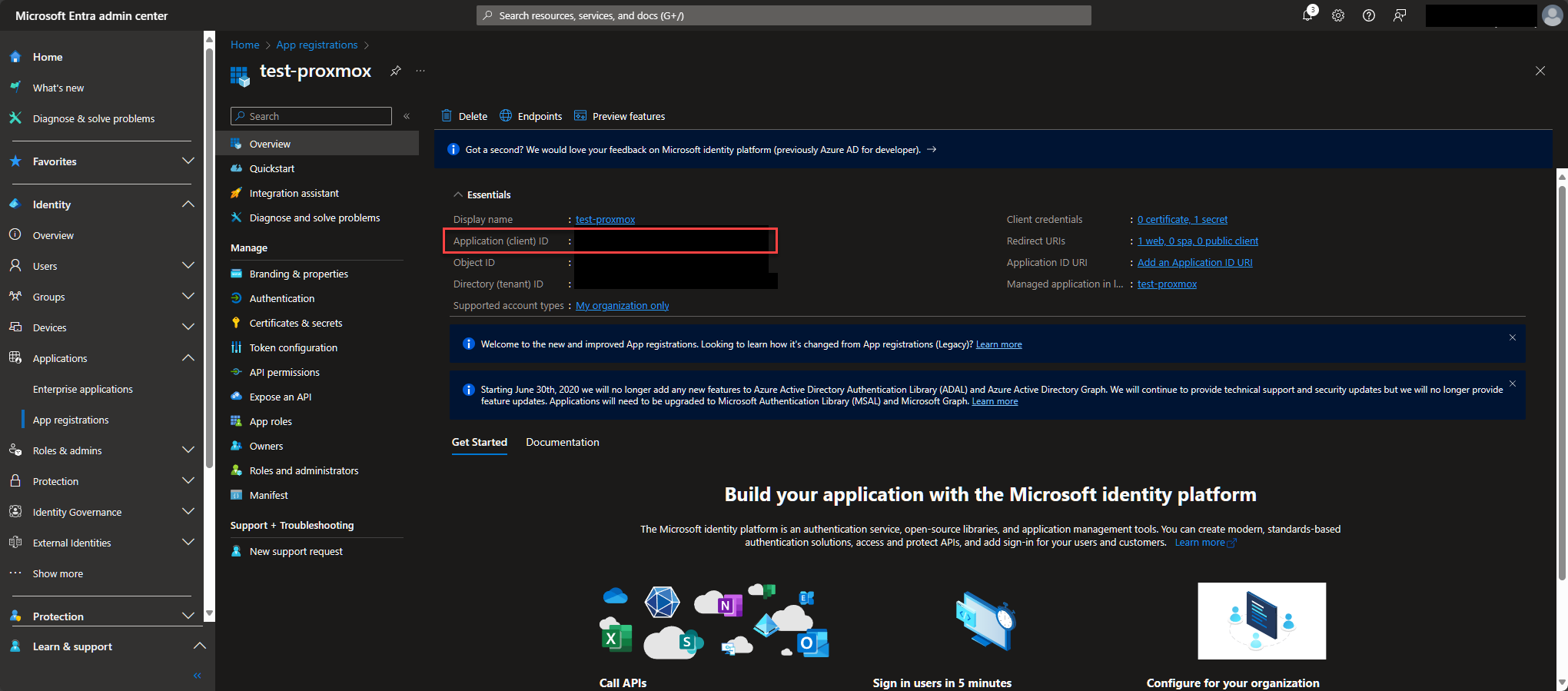
Click on endpoints and at the bottom for the OpenID Connect metadata document, copy everything before the .well-known so that your url should look https://login.microsoftonline.com/<tenantid>/v2.0 this will be used for Proxmox's Issuer URL field.
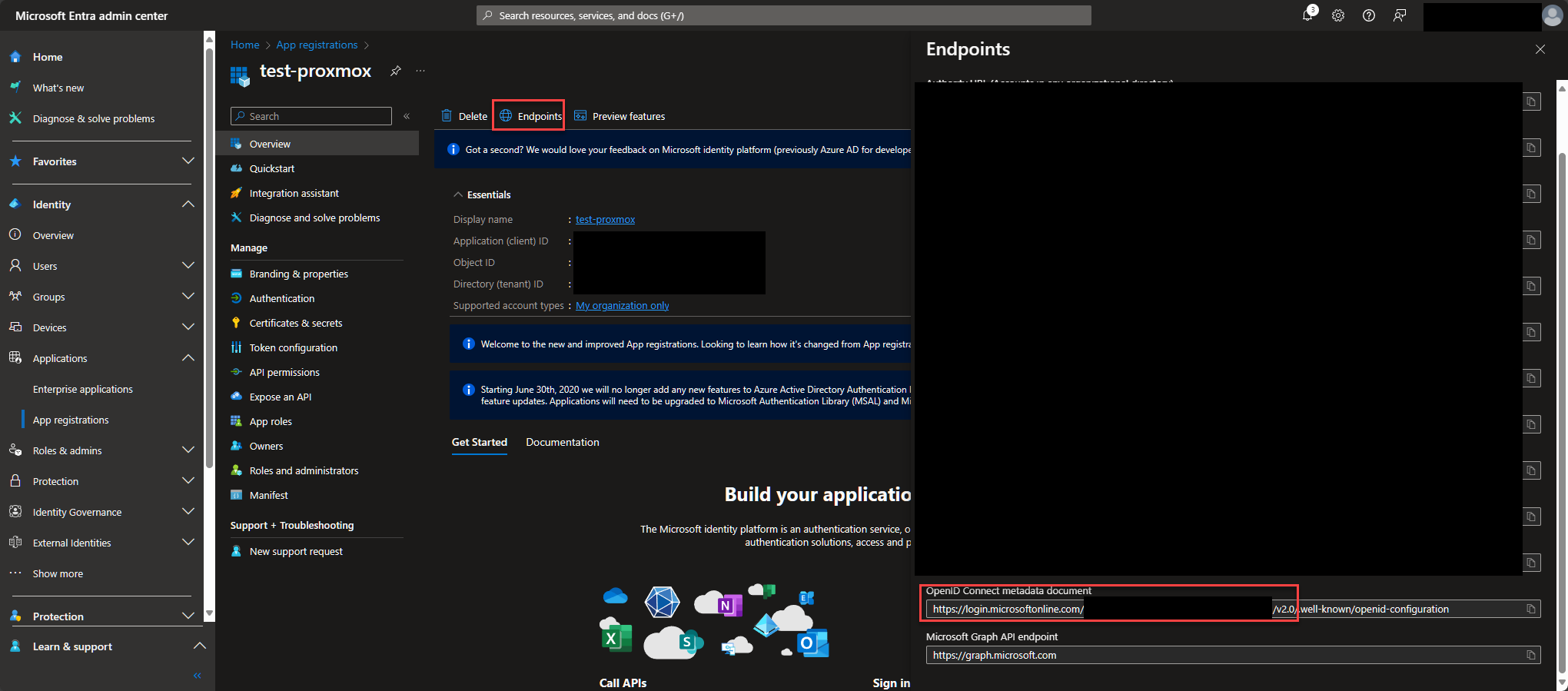
Now we have the bits Proxmox needs, let's head to that. Highlight the Datacenter on the left blade, in the middle Permissions -> Realms and finally on the right click Add then OpenID Connect Server.
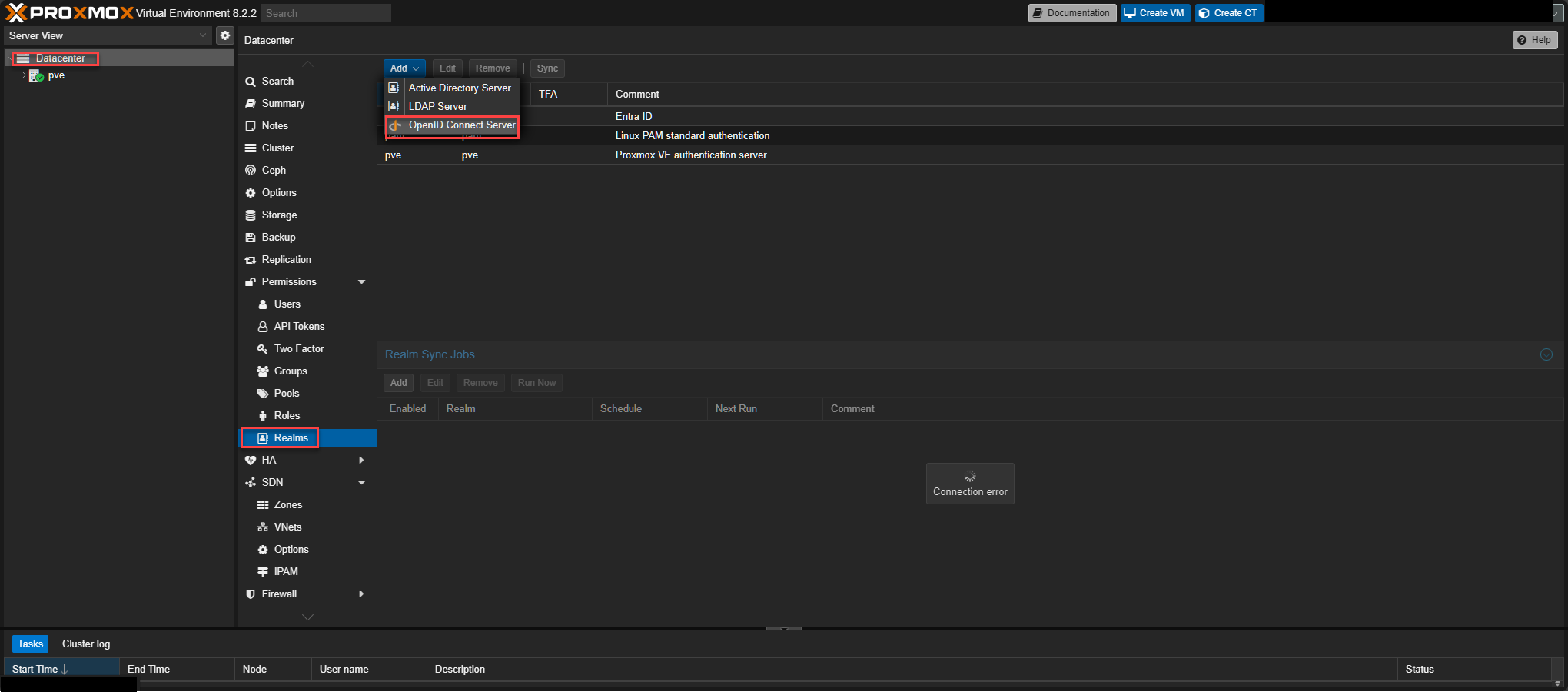
Enter the Issuer URL, Client ID, and Client Key fields from the values we grabbed in Entra. Realm is for your use to remember, but cannot be changed without making a new. Comment is what the user sees on login. Checkmark the Autocreate Users and Default checkboxes.
Now if we logout we'll see the login has changed with our new Entra as the default.
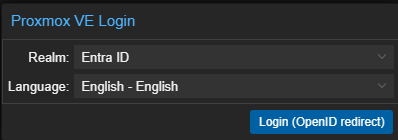
Click login, select/login as your Entra account, and now we see in the top right we are logged in but with no real PVE access.
So to resolve this, we logout once again. Change the dropdown to our Linux PAM realm, and login with our PVE admin credentials. In the Datacenter, go to Permissions -> Add -> User Permission.
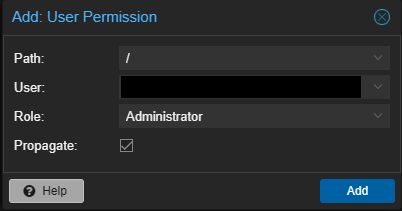
For the User select the same account string you saw in the top right when you logged in. If we want it to have admin for everything for Path do / and Role is Administrator.
After that, log out and then in with the Entra realm/SSO and you should see everything to administer once again.